Sun Tzu’s Five Factors and Cyber Security Strategy
Sun Tzu’s Five Factors and Cyber Security Strategy
I’m a big fan of Sun Tzu and also Wardley mapping, which uses Sun Tzu’s Five Factors. The way swardley summarises it and relates to the OODA loop is absolutely brilliant and how I like to think and navigate the business of defining a security strategy.
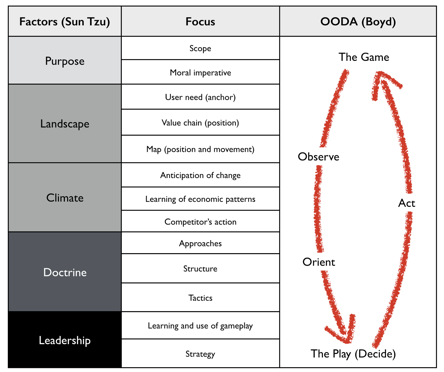
Given this structure I’ll be iterating through each of the Five Factors and the mental model I created from its application to Cyber Security.
Purpose
Purpose is your moral imperative. The things that drive what you wish to achieve. When I developed the ‘Map of Security’ mapping that was something I wanted to be targeted about and use Purpose to help frame the decisions and approaches we take.
Purpose is what we constantly need to come back to whenever situations arise and we need to make decisions (spend budget on X instead of Y as we had originally planned). It’s a reference to “what we’re here to do” and you’ll do well as a security leader if this purpose is consistently reinforced both with management peers and particularly with your own teams as the Purpose is what will drive behaviours.

The purpose is then to ‘achieve a secure state, relative to value and operational risk’. Not about implementing all the toys and controls, but rooted in an understanding of the value that is being protected, help in introducing measures to reduce risk.
It’s my belief that Cyber Security exists to ‘measure and prioritise business risk’ preferably through quantitative and not qualitative methods though this is still not the norm, frameworks such as OpenFAIR (which I blogged about here). For most organisations, Security is not about survival (I see that as actually making a sale which security doesn’t typically directly contribute to) but more on supporting survival by hopefully aiming for ‘reasonable assurance against predictable threats’.
And unfortunately, the Imperative for security in too many organisations is still on ‘Security as compliance’ nuisance as opposed to it being ‘Security as enabler of business’ and where I think there’s an overall tyranny of control culture among security professionals which is slowly changing.
Landscape
I think of landscape as the internals of the organisation. It includes things such as internal technology and control environment which will span the physical sites your operations span to, the people and security related practices.
It also includes internal politics and organisational structure, which may help or hinder the effectiveness of the security teams but nonetheless a key factor in making and sustaining change.
In a nutshell, it’s the typical people, process and technology.
In Wardley terms, it requires us to understand the user needs we are aiming to service, what the value chains of meeting those needs are and how each components relates to those value chains and how evolved they are.
Only by seeing a landscape, can we visualise a) options available to us (why of movement) and b) be deliberate about what we’re not doing.
Climate
Climate is about the forces which act upon our environment. A general PESTLE (Political, Economic, Social, Technological, Legal and Environmental) is appropriate in this space.
It’s key to anticipate change and understanding economic patterns. In the Economic and Technological space, that’s where adoption of Cloud native and Distributed, Immutable and Ephemeral design patterns are changing the role of the security professional as Sounil Yu extensively writes about.
It’s also about understanding the threat landscape and how it’s evolving. A particular report I include in my analysis is ENISA Threat Report
Something often missed from assessing Climate is an understanding of what your competitors are doing which I believe is key for security as enabler and to frame security with executive teams from a perspective of due diligence, appropriateness and if applicable even as product or service differentiator.
Doctrine
Doctrine, at its core, it’s about good management. Wardley frames it as “universally applicable principles regardless of climate or landscape”.
A big problem in most organisations is adoption of the latest “management secrets” literature when we have timeless principles that have served good management for millennia.
Wardley mentions adoption in Phases, though I’m aware of work in the Wardley mapping community to revisit this. Nonetheless, Benjamin Mosior LearnWardleymapping.com website has a great interactive summary you can use to RAG assess your practice (you shouldn’t necessarily believe in your assessment, but mainly how the team members believe those are being met. experience tells me there’s a world of difference between those two :))

All of these are key to building and sustaining effective and happy teams, and also relates a lot to psychological safety in the work place.
In Cyber Security, I also include here the training of people, standard ways of operating and working and the place of techniques you can apply though appreciate this makes it less “universal” and more context specific.
Leadership
Finally, Leadership is about understanding the gameplay and the options available. Business Gameplay has a better chance of being systematised than Cyber Security, mainly to the generations of body of knowledge which already exist and can be drawn upon. In Cyber Security, we don’t have that luxury as it’s a pretty recent “thing”.
Failing that, I believe considering Richard Rumelt’s “Good strategy/Bad strategy” Kernel of Strategy approach is particularly helpful for the security leader. I wrote about it recently in a LinkedIn post but for reference
Good Strategy has 3 elements:
- Diagnosis
This is about understanding facts and patterns of both Climate and Landscape. This should highlight what’s achievable and lead to an understanding of the adjacent-possibles which are available to us to help move the security needle in the right direction. Nothing leads to more failure of security leaders and security initiatives than the assumption that just because if fits your budget, you should be aiming for a particular project or transformation.
- Guiding Policy
This is the Policy that will be guiding the strategy itself. It serves to direct and serve as reminder of the what biggest opportunity is that should be leveraged. For instance if the diagnosis is that management of identities is the biggest problem affecting the organisation (it often is), then the Guiding Policy needs to reflect this diagnosis and define a number of goals which will be required to address the outcome of the diagnosis across all applicable dimensions (people, process and technology)
- Coherent actions
This is about focusing effort. Just because you have a budget that can fit attainment of multiple different goals and initiatives, doesn’t mean you should do it as not only will you find for yourself that items outside your diagnosis of what’s critical may steal attention away from the critical stuff (problem preference bias and the fact that if you did a good job of diagnosis, it’s going to be bloody hard to deliver on that objective).
Focused action means you can define and reinforce a clear message with stakeholders and teams to increase the odds of actually addressing it.
OODA
Thinking of the strategy cycle with an OODA lens, and specifically considering as iterative and not linearly as may be perceived from looking at the image above, means you’ll focus on the feedback loops which are helping you move forward in addressing the challenges identified in your Diagnosis and that you remain flexible and attentive to evolving situation and are prepared to apply your Leadership to navigate complex situations and keep the eye on the prize.