The future of Infosec is interdisciplinary and integrated
One of the themes you may have noticed from this blog and my talks, is the fact I tend to reference to mostly frameworks that sit outside of the traditional ones we tend to consider in Infosec literature and training.
Examples being Systems Thinking, Safety Science, Resilience Engineering, Wardley mapping, Team Topologies, Complexity and others. This is by design, not chance.
A few years back, I did some Wardley mapping where I went to check Job descriptions to try and figure out what were the commoditised skills in our industry (things everyone seems to “know” how to do), what was being requested by the market as “hot skills” needed and then went to check research on things which were emerging in research papers and new developments. This was back in late 2018/early 2019 that I made this research.
You can find the results below:
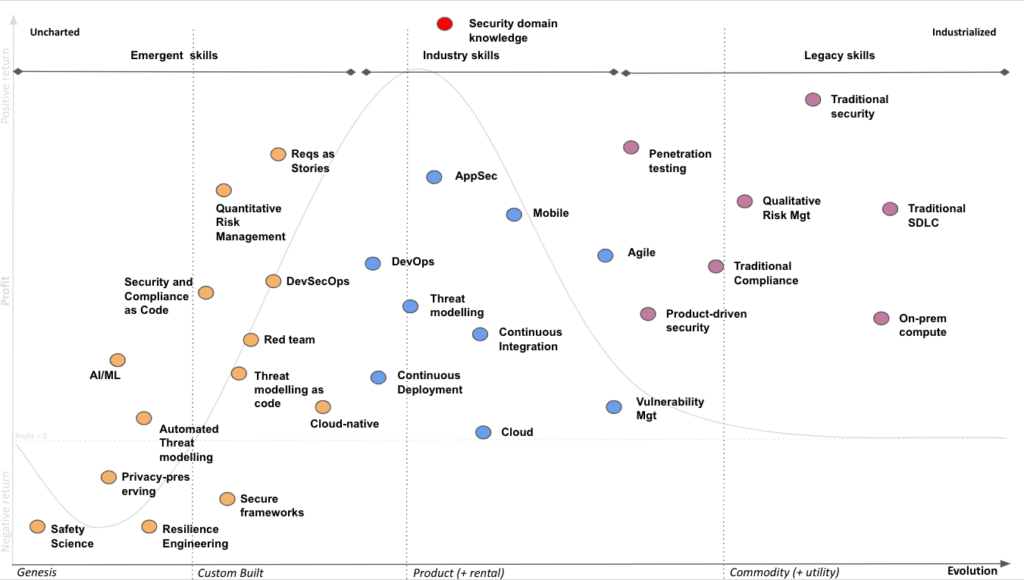
What I noticed from this was that most of the things which were emerging, weren’t really hard Infosec disciplines but more application of ideas from other areas on how to do security in a more integrated fashion, and that’s what I decided to focus on exclusively, as the areas I personally talk about. The rationale was that if I started talking about them early on, once the market caught up with it I’d be positioning myself as knowledgeable in those areas and with significant created content. For me personally, it started paying off earlier than I had anticipated.
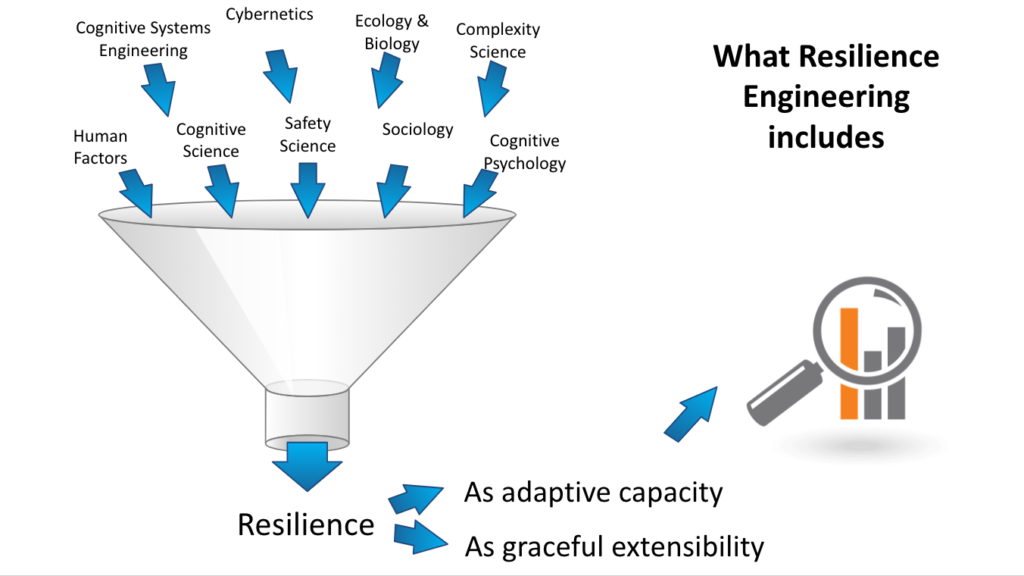
As a consultant, the clients I really wanted to work with with were finding me, instead of me looking for them. But particularly this year, in 2022, is when it all started coming together (3/4 years after I started), now that the market is catching up to the benefits of these and I’m being referenced by many as an expert in some of these, namely Safety Science and Resilience Engineering applied to Information Security (which I still struggle to see myself as such :))
Resilience Engineering in particular is a great “bang for buck” as it allows you to be exposed to a number of different fields of expertise highly relevant to understanding the organisations we wish to secure. They’re not hardcore Infosec practices, but we don’t really have good Infosec methods to either appreciate context or understand how organisations operate and develop. As Nancy Leveson says “Both Safety and Security are emergent properties of systems”.
We, Infosec industry, tend to like to think of Security as a series of specialist skills amalgamated together into a (hopefully) coherent whole, and in doing so we’re completely missing the underlying dynamics of how humans interact with each other which at the end of the day, is what makes or breaks your security programme and how drift from baselines occurs in otherwise robust systems
For more information on the above, you can check my slides on my latest “Security Differently” talk
This is the reason why it saddens me to see initiatives like the UK’s Cyber Security Professionalisation proposals going through UK Government at the moment, because I think they got it EXACTLY WRONG (which isn’t an easy thing to do), as if we were learning from Industry and the security unicorns out there (companies such as Netflix, Indeed, Spotify, etc), yes they do hire people in security specialisms but they have a focus in ensuring those directly involved in value creation structures have the minimum knowledge required to build secure software and systems at speed. Security artefacts and practices become SUBORDINATE to the value chains they wish to affect. By going down the road of specialisms, we run the risk of moving backwards from what the industry is telling us actually works, and go back to the “turf wars” and gatekeeping that have characterised our functions and arguments such as “I am a $narrow_role and a $narrow_role does X and does not do Y”. Security and security activities are HIGHLY contextual, and focusing on narrowly defined specialisms fosters expectations of certain types of artefacts and hand-offs and has the potential to set back true integration of security outcomes and objectives into the value creation structures we should be supporting, and not mandating.
What I’ve been seeing in the last few years, is suggesting that I didn’t get it too wrong on that original Wardley map I’ve created. Team Topologies and the idea of Enabling teams with certain characteristics, is getting a lot of us better at being provisioners of capability as opposed to requirement setters, writing uncontextualised policy documents that no one knows they exist in our organisations and then holding them culpable (we tend to call it accountable) when those requirements set with poor understanding of operational context aren’t met.
I believe the future of this industry has to necessarily be multi-disciplinary (and one of the reasons we need more career changers particularly from backgrounds such as QA, development, sociology, anthropology, etc) so we can start getting better at making sense of our context and how humans make decisions and are affected by goal conflicts and constraints, and it has to be integrated because we can’t just expect to have armies of specialised resources delaying and introducing friction into value creation structures, which is the natural byproduct of overfocus on specialisms.
I do hope the great things I’ve been seeing in this industry continue, that I’m wrong about the direction of travel in the UK and the unintended consequences their professionalisation approach may bring, and that overall our industry gets to understand our traditional gatekeeping approaches are no longer appropriate for a fast moving, complex world where our companies can no longer choose between being fast or being secure, that we understand that moving fast and being secure are actually mutually supportive, not mutually exclusive… if we just approach it in an integrated way
As Laksh Raghavan shared on Twitter, a great quote by Prof. Feynman sums it up nicely.

As I keep saying, specialisms are about doing the “work of security” not on enabling the “security of work” and the outcomes we are after depend more on the latter than the former.